So, I’ve had a problem converting the ASA’s site 2 site tunnels from Policy Based to Route Based – when trying to create the tunnel from the Azure side, the cryptomap presented from Azure is local: 0.0.0.0/0 remote: 0.0.0.0/0, and if you make a VPN tunnel on your ASA with this crypto map, the ofc. all traffic will go into the tunnel, and you cannot acces the internet anymore, unless that breaks out in Azure.
So the setup need to be changed on the ASA to support a any/any crypto map and only route the traffic that actually resides in Azure through that tunnel. Looking at how routers do this, is by creating a Tunnel interface and route traffic towards Azure through this interface – so I will show here, how i mirrored that approach to the ASA.
Azure details, will be short and without screenshots:
Create a new Virtual Network Gateway
Atleast VpnGw1 SKU
Route Based
Create a Local network gateway
IP Address: WAN IP of you local ASA
Adress Space: On-Prem subnets
Create the VPN
Go to Virtual Network Gateway -> Connections and Add a new
Connection Type: Site-to-Site (IPSec)
PSK: Set this to whatever you choose – and remember it for the ASA config
The ASA:
(Guide currectly only for ASDM)
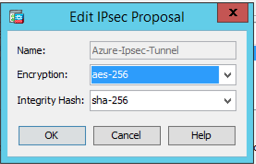
Configuration -> Site-to-Site VPN -> Advanced -> IPSEC Proposals (Transform Sets)
Add a new IKE v2 IPsec Proposal
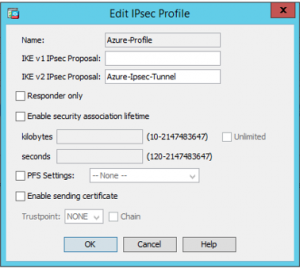
Add a new IPsec Profile
Apply
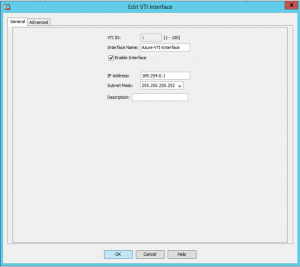
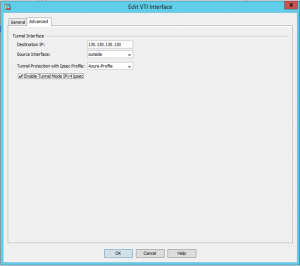
Go to Configuration -> Device Setup -> Interface Settings -> Interfaces
Add new VTI interface
Apply
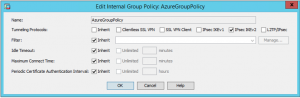
Go to Configuration -> Site-to-Site VPN -> Group Policies
Create a new Group Policy
Apply
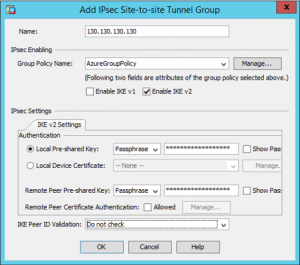
Go to Configuration -> Site-to-Site VPN -> Advanced -> Tunnel Groups
Add a new Tunnel Group
Apply
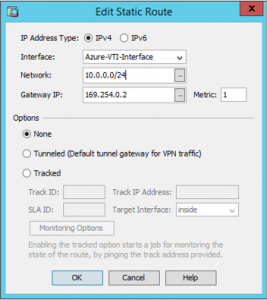
Go to Configuration -> Device Setup -> Routing -> Static Routes
Add a new static route
Apply and Save Configuration
Microsoft recommends 2 additional settings:
Go to Configuration -> Firewall -> Advanced -> TCP Options
Set this
Go to Configuration -> Site-to-Site VPN -> Advanced -> System Options
Set this